How to Protect Work Emails During Coronavirus Pandemic
Following our article on top phishing scams to avoid during the Covid-19 epidemic, I thought it would be good to follow up with some advice for organisations on protecting their employees from falling for these scams.
The advice here is not unique to a pandemic. Organisations can implement these measures to support a wider cybersecurity strategy. It’s easy for me to say: “now is not the time to reduce cybersecurity budgets” - I know that isn’t practical considering some businesses have been squeezed to their absolute limits; however, that doesn’t mean IT leaders and C-Suite executives can’t get creative with budgets to ensure that special attention and the right resources are given to email security.
Of course, the UK has been easing lockdown measures but I expect many organisations and institutions will be encouraging employees who can continue to work from home, to do so. That being said, there will be a mixture of internal and external employees going forward, so organisations will have a more complex network to secure, making email security increasingly complicated.
Accounts and Access
All staff need user accounts and access to corporate networks. Whether you’re a large organisation managing these things with Active Directory or you’re a small organisation managing access to each SaaS service individually, staying on top of access rights and user management is a key component to ensuring successful cybersecurity programs.
Here are some rules for access management:
- Employees must only access what they need to do their jobs.
- Access must be revoked when they leave the organisation.
- Access rights must be managed and maintained by a central admin user.
- Admin users must have stricter access requiring multi-factor authentication and stronger passwords.
- Admin access in the organisation should be kept to a minimum and only be granted to trusted employees.
- Good password management tips and training should be given to employees.
- Multi-factor authentication should be required for most sensitive access (i.e. to the CRM or financial databases).
How do these measures help protect work emails? If an employee falls for a phishing email that downloads a keylogger, for example, a hacker can get access to the usernames and passwords being entered by employees on a daily basis.
By ensuring users only have access to what they need, putting extra barriers around more sensitive data and minimising the number of admins, you reduce the likelihood that an attack can lead to a data leak. Of course you don’t want to get to the point where an employee’s email is hacked, but it’s always better to be prepared for the inevitable.
Encryption and Authentication
I actually wrote a blog on 4 different ways you can encrypt email in your educational institution. But to summarise and broaden for a wider industry, I talked about:
- S/MIME – using S/MIME certificates to identify senders and encrypt emails.
- PGP – using PGP to encrypt and verify emails.
- TLS – to encrypt the connection between servers.
- PDF Encryption – to protect attached documents from being read or altered.
Usually, a mixture of these elements will be required. I mention in my article that it’s not enough to simply encrypt the connection because the connection can be compromised. It’s also not enough to encrypt the message because you still cannot be certain the recipient will receive the email in the way that you delivered it.
The difficulty that SMEs will have in delivering a fully encrypted email solution is deploying and integrating the right technology for the job. Gmail and Microsoft do not cover all these grounds on the basic level and it can get very expensive when purchasing business or enterprise licenses for every employee.
Thus, it is inevitable that SMEs will have to get creative and look for solutions that they can trust to fill the gap within their budget.
Scanning
All outgoing and incoming emails need to be scanned for viruses and phishing. A typical set-up for an encrypted incoming email looks something like the below images:
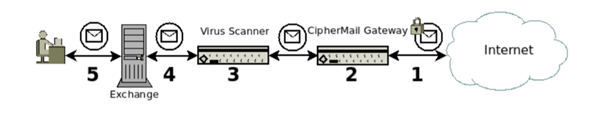
- S/MIME encrypted message is received from the Internet.
- CipherMail gateway decrypts the message.
- The decrypted message is scanned for viruses.
- After virus scanning, the message is forwarded to Exchange.
- User reads the message.
A lot of email tools struggle with scanning encrypted emails since a decryption key is needed and encryption needs to happen before sending the email on to keep security. I’ve discussed this in more detail in another post where I said:
“Instead of scanning for spam or viruses after the message was accepted, a better option would be to reject email at delivery time before accepting the email (i.e., place the anti-virus anti-spam scanner between the Internet and the email encryption gateway). When a message is flagged as spam, the sender will be notified that the message was not accepted.”
Email scanning should be able to scan links and URLs, scan for keywords in the header and content that are used frequently in phishing and quarantine or flag emails to employees that it deems are dangerous. This makes it easy for employees to see which emails have been flagged and delete them or flag the email as safe to the tool so that emails from that sender are not flagged again.
Data Loss Prevention
Another important feature to protect work emails is the use of a data loss prevention (DLP) feature. DLP tools will be responsible for scanning outbound emails for keywords, recipient emails, data and URLs that can trigger a certain response from the email tool.
For example, from the admin level, encryption can be forced on emails that include the word “password” because you might assume that there will be sensitive information in those emails. You will be able to action incoming emails that meet your configured requirements in the following ways:
- Warn - send an email containing a warning. Depending on the DLP settings, the warning email will be sent to the sender of the email and/or to the DLP managers.
- Encrypt - flag the email to mandatory encryption. When flagged, If the email cannot be encrypted, the email will not be sent and the sender will be notified.
- Quarantine - put the email into quarantine. Depending on the DLP settings, the sender of the email and/or to the DLP managers will be notified.
- Block - drop the email, i.e., the email will not be delivered. The sender of the email will be notified.
It’s important to note that quarantined emails are not delivered to the recipient's inbox, greatly reducing the risk they will be opened on the end-users' (employee’s) device and potentially spread a virus or malware.
There is some work involved for admins when it comes to creating DLP rules that best secure the organisation but the great news is that employees don’t have to do anything at all. This helps employees feel secure without having the burden of new processes and tools they have to learn how to use, especially in a time where there is already so much to worry about.
Archiving and Compliance
Organisations will have complex regulatory landscapes to navigate – many of these can be helped by DLP. For example, you can look for financial information in emails and force encryption on those to meet the demands of the PCI DSS regulation.
Ultimately, organisations need a way to analyse and archive their email databases. Across a wide range of industries, data security and retention are critical when it comes to regulatory compliance. Depending on your particular industry, there will be specific rules for email archiving compliance and how to store data and documents.
Archiving your emails on an organisational level allows you to store this data in a way that is easily accessible and where retrieval is in its original format—making data compliance simple for your business.
Organisations often fall into issues when their email tools archive encrypted emails as the retrieval of these emails in the future is fraught with difficulty. To access the encrypted emails, a decryption key is needed and finding the key after archiving the emails for years is a struggle many organisations have faced. A better solution would be to decrypt the email before archiving and encrypt the entire archive instead. I explain more about how this works in another blog.
Training and Awareness
No security strategy is effective without proper implementation, training and awareness for employees. If you’re taking on a new tool to meet the gaps your current email infrastructure has, go for something that is going to take less time to implement and make the least difference to the end user. That way, employees need little training on the new processes and you can ensure that business as usual is a little more secure.
During this pandemic, more than usual, IT admins can make employee life a lot easier by documenting processes and creating as many guides as possible. That way, when employees experience difficulties at work, they can be guided to easy to read documentation and support is not overrun with tickets.
Another effective tool is known as phishing simulation, where you can create fake phishing emails and monitor employee responses to flag specific teams or employee’s who are repeat offenders and give them additional training.
This may not be helpful to implement during the pandemic as it’s catching people out who are already struggling, but it will be an effective tool when organisations start to ramp up again after the lockdown measures are fully eased.
