Avoid Employees Falling For These Coronavirus Phishing Scams
Whether or your business is suffering or booming in these times, the impact of coronavirus has no doubt made organisations rethink many strategies and processes in order to maintain commerce and keep cash flowing. Will you be able to survive the impact?
One of the areas that poses a great risk to organisations is their handling of cybersecurity. Leaving your doors open to a cyberattack could be the difference between staying in business and having to close your doors; either because you’ve breached data protection laws and have fines that you can’t afford to pay, because your data is held ransom or because a cybercriminal has sent a virus into your systems that impacts your ability to operate.
On any given day, Google blocks 100 million phishing emails and as many as 20% of them are coronavirus phishing scams. Luckily Google has good machine learning tools that are able to block a lot of these emails but what happens to the small minority that make it through?
Not everyone uses Google and Microsoft for email management, this is where small businesses are likely to feel the burn if they don’t pay to use Google and Microsoft’s full suite of email features.
One of the most popular methods for hackers at any time, but especially during the Covid-19 pandemic, is phishing. Email phishing is carried out in many ways, some you may recognise include:
- Sending an email from a known address containing a virus in an attachment.
- Sending a regular looking email like an invoice in order to redirect funds or acquire sensitive financial data.
- Sending an email from what looks like a government body or financial institution asking for passwords, financial information or sensitive data in any form.
Organisations have all kinds of employees, from people who are tech-savvy to those who are less capable. And even the tech-savvy have been known to fall for phishing scams so it is not enough for businesses to simply trust that employees will do their best. A sophisticated approach, which includes training and awareness are needed for organisations to reduce risk.
A simple approach to start with is to give guidance to employees on how they can spot a phishing email and what they should do when they spot one (e.g. report it to IT). It’s important to remember that your organisation can fall victim, even if the phishing email was opened on an employee’s personal email account, so this should be factored in when creating processes and training employees.
Here are a few scams I have noticed that should warrant some attention from organisations.
Government Relief Packages
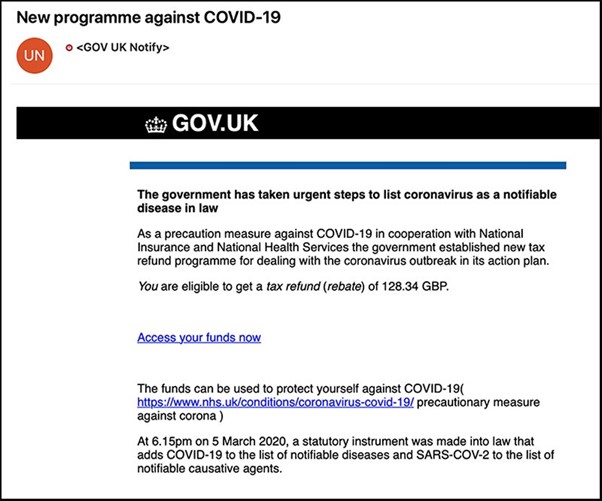
Clicking on “access your funds now” would take you to a fake government web page encouraging users to input all their tax and financial information. It’s important to remember that the government will never ask you for this information over the web or over the phone.
World Health Organisation Impersonating
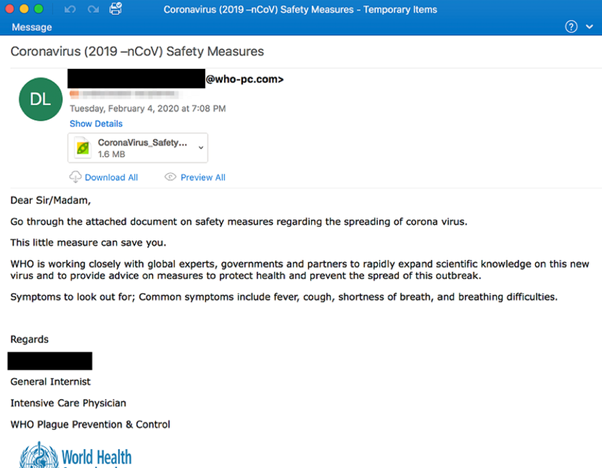
The bad grammar and email address are the first signs of something suspicious. The WHO-pc.com? That is not the official domain for the World Health Organisation. Also why would the WHO email me directly with an attachment? They would be more likely to publish their advice online.
The attachment contains malicious software called AgentTesla Keylogger which records every keystroke and sends it to the attackers, a tactic that allows them to monitor their victims' every move online. If that keylogger is downloaded in the work network without any IT monitoring in place, the attackers would be able to access all the accounts of the employee as they go about their daily work activity.
Spoofing a Government Entity
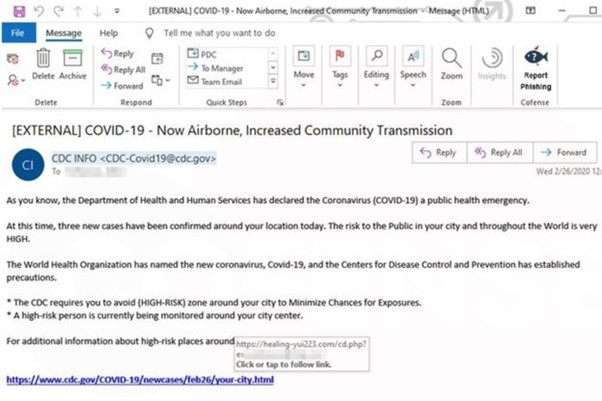
This email is sent from a legitimate CDC domain which means that the hacker was able to spoof a real email address. This tactic makes some phishing emails even more successful and harder to catch.
The attackers are using fear and panic to increase the likelihood that a user will click their link. The link takes them to a Microsoft email login page which redirects to a real CDC advice page, making it look even more legitimate but of course, once there, the hackers have access to your email account.
Appealing to Generosity
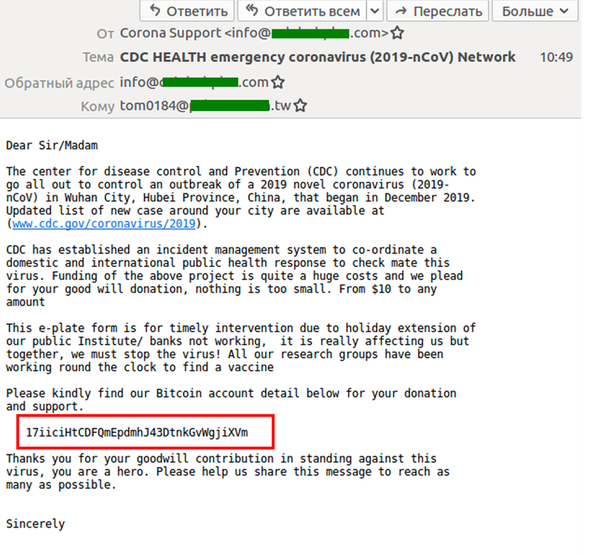
This example is another fake CDC email reported to Kaspersky. The email asks for donations to develop a vaccine but requests the payment is made in Bitcoin which should raise some eyebrows.
Click For a Cure
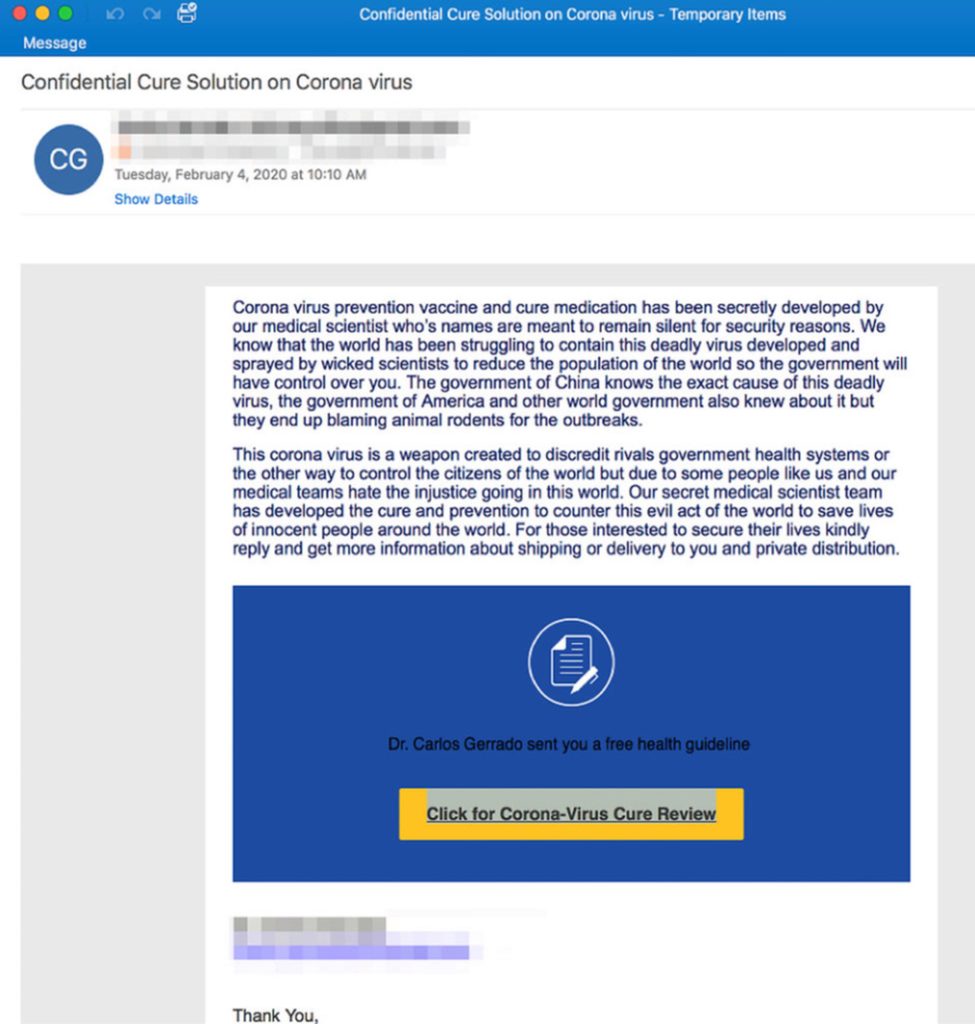
This example has been around since February 2020 and is preying on people’s suspicion and paranoia. It plays on a conspiracy theory about a Chinese government cover up and encourages people to click for a cure. These emails are sent to hundreds of thousands of people at a time and the fake website you land on when you click the link will be designed to steal your personal details.
Email Gateway Tool
Organisations wishing to increase their cybersecurity capabilities and create a more robust monitoring infrastructure for incoming emails without the cost of Google and Microsoft’s full features should look into a compatible email gateway option. Used as an integrated tool you could reduce the risk of falling victim of a phishing scam with:
- Inbound email scanning (including text and attachments).
- Machine learning threat detection.
- Email encryption and signing to further verify identities.
- Email monitoring and filtering.
- Policy management from an admin level.
- Data leak prevention features.
All of these features can be gained with a very easy installation process for the organisation. Recipients do not need to install anything on their end to gain the benefits of email encryption.
Pie Security is an email encryption gateway. For more information on its features and benefits, visit our solutions page.
