New Industries Should Get Ready to Comply with the Revised Directive on Security of Network and Information Systems (NIS2)
The moving world of regulations is a headache best placed with risk managers and compliance officers. But in truth, business owners need to be aware of what regulations they’re business is required to comply with too, especially when those regulations change so frequently.
One such regulation revision is the Directive on Security of Network and Information Systems. NIS as it is called, is now being upgraded and companies need to be ready for the second iteration – NIS2.
What is the Directive on Security of Network and Information Systems (NIS)?
NIS 1.0 came into force in 2016 and was the first European regulation on cybersecurity. It aimed to provide measures that would boost the overall cybersecurity of the EU. Some of the main requirements included:
- Requiring member states to form a Computer Security Incident Response Team (CSIRT) and a NIS authority.
- Setting up a cooperation group to facilitate strategic cooperation and the exchange of information among Member States.
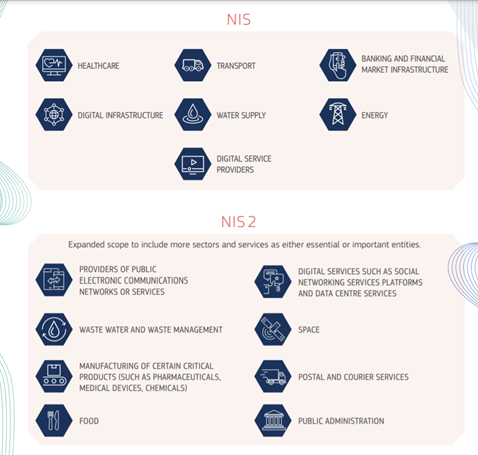
- Having a culture of security across sectors that are vital for our economy and society and that rely heavily on ICTs, such as energy, transport, water, banking, financial market infrastructures, healthcare and digital infrastructure.
- Requirement on sectors mentioned above in key member states to take appropriate security measures and notify relevant national authorities of serious incidents. Key digital service providers, such as search engines, cloud computing services and online marketplaces, will have to comply with the security and notification requirements under the new Directive.
Consultation and review
On the 7th of July 2020 a consultation of the legislation was opened up with a close date of 2nd of October 2020. The results of the consultation went into creating a new legislative proposal, presented on 16th of December 2020. The proposal will be subject to negotiations between the co-legislators, notably the Council of the EU and the European Parliament and once agreed, will be subject to adoption 18 months later.
What’s new?
Communication sharing
On top of the existing CSIRT and NIS authority, the NIS2 regulation proposes the creation of a EU-CyCLONe (European Cyber crises liaison organisation network) to coordinate large scale cyber-incidents at EU level. EU-CyCLONe, CSIRTs and NIS Authorities will form a corporation and information exchange which includes the sharing of best practices and guidance to organisations and the sharing of vulnerability disclosures. The sharing of vulnerability disclosures will probably compete with the US NIST vulnerability database.
Risk management
The European Commission also say there will be changes to address cybersecurity risk in supply chains:
“Furthermore, the Commission proposes to address security of supply chains and supplier relationships by requiring individual companies to address cybersecurity risks in supply chains and supplier relationships. At the European level, the proposal strengthens supply chain cybersecurity for key information and communication technologies. Member States in cooperation with the Commission and ENISA, will carry out coordinated risk assessments of critical supply chains, building on the successful approach taken in the context of the Commission Recommendation on Cybersecurity of 5G networks.”
Strengthened security requirements will be included with a list of focused measures including incident response and crisis management, vulnerability handling and disclosure, cybersecurity testing, and the effective use of encryption. There will also be accountability for company management for the effective compliance with these risk management measures and added incident reporting requirements with more precise provisions on the reporting process, content and timeline.
New sectors
Finally, the sectors covered by NIS and NIS2 will vary greatly. Many new sectors are being added to the NIS2 directive:
- Public electronic communications and network services.
- Digital services such as social networking platforms and data centre services.
- Wastewater and waste management services.
- Manufacturing of critical products such as pharmaceuticals, medical devices and chemicals.
- Postal Services.
- Public administration.
End-to-end encryption
Any providers of services listed in the industries above will soon be promoted to use (and in some cases mandated to use) end-to-end encryption in their products and services in accordance with the principles of privacy by default and design. An interesting caveat to this is that the wording adds an exception:
“The use of end-to-end encryption is without prejudice to the Member State’ powers, policies and procedures to ensure the protection of their essential security interests and public security, and to permit the investigation, detection and prosecution of criminal offences in compliance with Union law. Solutions for lawful access to information in end-to-end encrypted communications should maintain the effectiveness of encryption in protecting privacy and security of communications, while providing an effective response to crime. Any action taken has to strictly adhere to the principles of proportionality and subsidiarity.”
It will be interesting to see how companies try to implement secure end-to-end encryption while also creating a security gap that the EU can use to investigate criminal cases. This technically isn’t the definition of end-to-end encryption.
Email Security at Heart
With email still the number one risk to organisational security, companies should have a look at the gaps in their email security solutions. Microsoft alone cannot protect you. As we know hackers are already using the Microsoft brand to trick employees into giving up their login details. Once a hacker has access to an email account, they can go undetected for some time while they gather up the relevant knowledge to strike. I discuss this more in another blog about Business Email Compromise (link).
SMEs already have stretched IT teams so a delivered cloud solution like PieSecurity is a must. PieSecurity has a combined 75 years’ experience in email security and UK, EU privacy laws. Our solution can be delivered in the cloud or on-premises and requires no knowledge to get started.
PieSecurity is fully compliant with EU regulation and has multiple encryption features such as S/MIME, PDF Encryption and TLS Encryption for a multi-layered approach.
To learn more about our email security solution and its features, visit our website.
